
Frictionless Access Bridging the Gap Between Physical and Digital
By Paul Aronhime, VP of Federal & Commercial Sales, IDEMIA I&S North America
Today’s businesses and government agencies are operating in an increasingly digital world accelerated by the pandemic. To safeguard various types of transactions these organizations must be able to verify the identities of their customers and users online and remotely validate that people are who they say they are. This virtualization of identities has been in process for many years and has resulted in identity technologies that support high levels of identity assurance through multimodal authentication mechanisms. Further, digital identities are fast becoming the dominant secure transactional currency. From opening and accessing accounts to online registrations and payments, today people are more likely to leverage their digital identity for almost everything in day-to-day life. People are increasingly more accustomed to the ease of online-centric services.
In the physical world proving identities using government issued picture IDs is straight forward, whereas in the digital world this process becomes much more complex. This complexity increases the likelihood or need to establish immutable identities rather than physically presenting a single document during in-person engagements. A digital identity encompasses unique identifiers and behavior patterns tied to an individual; it is a combination of the digital presence one creates through activities including participation in social media and mobile phone location services that can be taken holistically to attest to who we are.
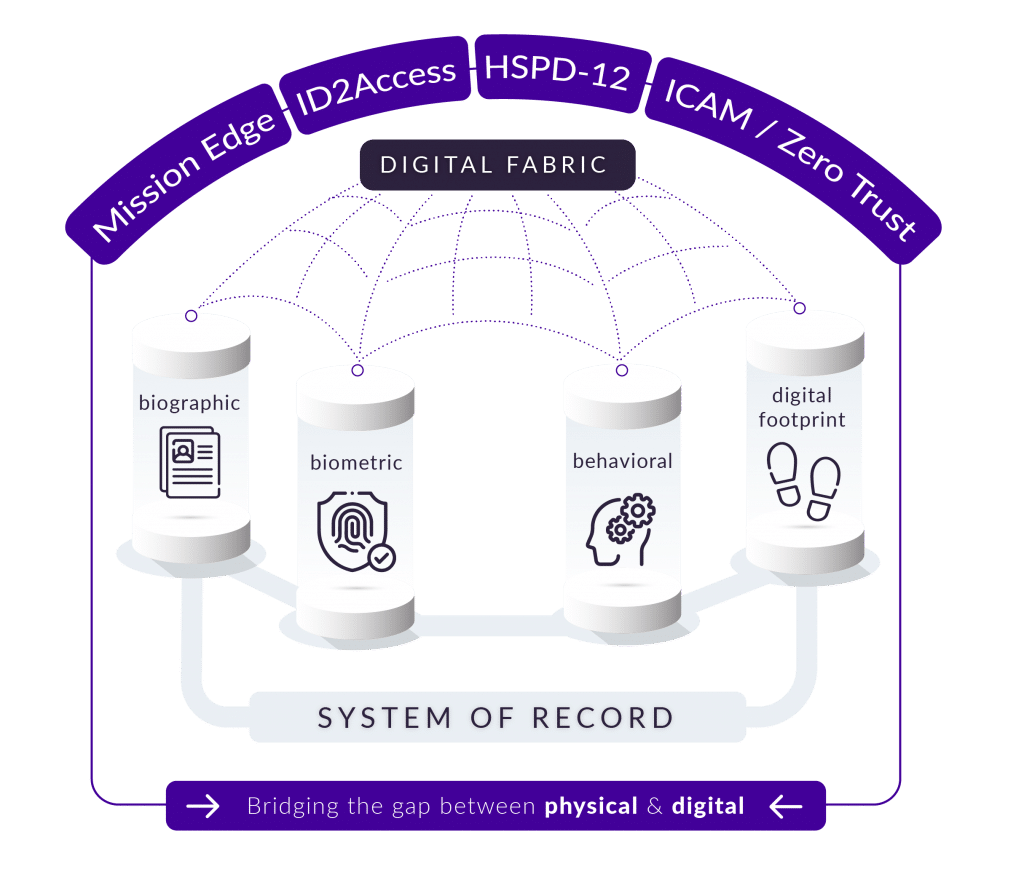
An individual’s existence is often characterized through digital attributes that begin as early as birth. Names, birthdates, social security numbers, street addresses, email addresses, and medical histories work together to represent who a person is. Attributes must often be combined to assert the uniqueness of a given identity. Facial images, fingerprints, driver’s license, where others are more unique, such as the SSN. They all can work together towards defining a single individual. Biometric images and templates are also digital attributes that encompass biological aspects and physical features unique to a person. Faces, fingerprints, irises, voices, scarring, birthmarks, and tattoos can be seen as unique features, attributable to one unique person. Finally, digital attributes may include authoritative credentials from trusted third parties that attest to one’s identity. These credentials rely on the previous digital attributes—PII and enrolled biometrics—to be a valid source of identity verification. Digital activities contain online digital footprints, such as social site likes and shares, photos, purchase history, and mobile phone usage.
Theft of personal identity information (PII) is rampant due to exploits by bad actors taking advantage of static data verification methods such as “something you have” and “something you know.” These techniques are proving insufficient as identity proofing techniques. Things that you have, such as ID cards, can be lost or stolen; and things you know such as passwords and security questions are sometimes shared or could be compromised and become purchasable on the dark web. What is needed is a method for upfront identity verification and ongoing user authentication. Interconnecting these processes can be achieved by integrating digital attributes and activities into a holistic multi-modal system to support the collection, aggregation, and proofing of multiple elements to form an identity fabric on a single platform. This fabric allows for previously verified identities to be confirmed through both active and passive methods, reducing the burden placed on users by traditional multi-factor authentication methods. It also enables attestation to only what is required for a specific transaction without exposing additional, non-essential information.
The concept of a multi-modal identity fabric for initial and continual identity verification is illustrated in the following hypothetical scenario: John is a contractor working in the defense industry and will be attending a meeting at a nearby military installation. His meeting sponsor within the Department of Defense (DoD) initiates the visit and requests John to submit the required biographic and credential information to conduct a background check and register with force protection for the installation. Previously, John would have submitted this information via email to his point of contact (POC), who has the information vetted. When John arrived at the installation, he would have gone to the Visitor Control Center (VCC), presented his identification, had his photo taken, and received a pass to enter the facility. However, using a digital identity platform streamlines the enrollment, vetting, and access process using a cutting-edge identity fusion system that combines best-in-class biometric, credential, and biographic information to enable near-instantaneous vetting and rules-based facility access. Using smart technologies, the facility can address potential threats while enabling secure but flexible access, with continuous vetting as John travels throughout the facility.
This concept can be achieved through simple actions of the visitor. First, John (visitor) leverages his smartphone to take photos of his credential, face / selfie photo, and fingerprints. His credential is validated visually, as well as through automated checks against the issuing authority. His facial biometrics are matched to his credential, including full liveness detection. Once John has been verified, his biometrics and biographic data are vetted against established systems of records (SOR) in government and third-party databases. The results are then verified back into his consolidated identity. At this stage, John is ready to access the installation, and can do so without having to visit the VCC since the information was collected remotely. John uses his biometrics, either his face or fingerprints, to authenticate himself at the access control point. The access points leverage biometrically enabled fast lanes to reduce congestion and improve traffic flow by performing vehicular based real-time facial recognition on the move. The key outcomes of the platform include:
- Reduced bottlenecks at access points using “fast lanes” with contactless biometric fingerprint and facial recognition technology.
- Increased real-time situational awareness of personnel and visitors at entry and while on the installation using biometrically verified credentials.
- Improved overall installation safety.
- Enhanced security of mission-critical assets and infrastructure using identity resolution, continuous vetting, and insider threat risk reduction solutions.
The value of this holistic and frictionless digital identity solution isn’t restricted to single points of interaction like access control; it enables enhanced real-time situational awareness, improved safety and security, and increased efficiencies. Whether leveraging current infrastructure or Intelligent video surveillance systems, it provides this awareness beginning with the identity verification and risk assessment process beyond the physical perimeter—reading license plates and identifying faces as vehicles and pedestrians approach the access point. This same solution can be applied to interior spaces, where the pattern of life of known individuals can be monitored and deviations from expected patterns, such as where an individual enters a restricted zone, can be used to alert security force personnel. These capabilities can be achieved through centralized video processing of preexisting surveillance feeds or pushed to the edge through an embedded alerting platform. This will become especially useful with the expansion of dedicated wireless Internet of Things sensors. Enabling cameras to operate with edge processing and send data to central cloud services for data aggregation across the enterprise. It is with these features that we can apply a Zero Trust architecture or even an ICAM solution to physical security to ensure that physical authentication mirrors the capabilities of virtual interaction. This is just one example of how identity can be leveraged. Similarly, we can apply an identity / biometric solution to better secure and gain access to a network, applications, and data – pushing the identity fabric to the edge, bridging the gap between physical and digital.



